
Managing Information as an Enterprise
"I thank you for the trouble you have taken in forwarding the intelligence which was enclosed in your Letter of 11th of March. It is by comparing a variety of information, we are frequently enabled to investigate facts, which were so intricate or hidden, that no single clue could have led to the knowledge of them in this point of view, intelligence becomes interesting which but from its connection and collateral circumstances, would not be important."
General George Washington
Letter to James Lovell
1 April 1782
"The unqualified importance of information will not change in 2010. What will differ is the increased access to information and improvements in the speed and accuracy of prioritizing and transferring data brought about by advances in technology. While the friction and the fog of war can never be eliminated, new technology promises to mitigate their impact."
Joint Vision 2010
Chairman of the Joint Chiefs of Staff
A Virtual Collaborative Intelligence Environment
The national intelligence enterprise of the 21st Century must provide the knowledge needed by its customers, wherever they are, to enable the decisions they must make and the actions they must take.
Foreword
"The possession of facts is knowledge,
the use of them is
wisdom."
-Thomas Jefferson
This paper will not introduce anything particularly new regarding information technology to those well informed in the progressive capabilities it enables. Instead, it presents a message to Intelligence Community leaders to capture the moment to expedite progress in exploiting those capabilities. They must do so to effectively manage the Community's most important resource (its information) to produce the more agile intelligence enterprise envisioned for the 21
st Century.Outlined herein are relevant considerations, planning factors and guiding principles for an evolutionary strategy to support future program decisions. The Community has produced a strategic plan for information systems that applies those principles to guide information technology investments and enable the nation's Intelligence Community to become more efficient, effective, and agile.
In an increasingly chaotic international environment, doing nothing is not an option. If the Intelligence Community fails to adapt to the realities outlined, it risks becoming obsolete.
Preface
Our Challenge
Managing Information Support to Our Missions
Support to National Policymakers
Support to Military Planning and Operations
Support to Law Enforcement
Support to Counter Foreign Intelligence Activities
Potential Mission-Support Scenarios of the Future
Additional Challenge of a Dynamic Environment
Rapidly Emerging Technology
Information Explosion
Declining Resources
Unstable Geopolitical Environment
National Security Shifts
The Changing Role of Government
Turning a Challenge Into an Opportunity
Becoming a More Agile Enterprise
Enabling Components of an Agile Enterprise
Distributed Collaboration
Information Service Capabilities
A Common Telecommunications Infrastructure
An Integrated Information Space
Facing the Challenge-Seizing the Opportunity
Manage our Information as a Critical Community Resource
Exploit the Opportunities Offered by Information Technology
Invest More Prudently in Information Technology
Conclusion
Preface
Intelligence service in the United States is a multi-billion dollar federal enterprise vitally needed for the continued security and prosperity of our nation. It is undergoing tremendous change as we near the close of the 20
th Century. Complex and rapidly changing intelligence targets and missions are evolving in a new international environment. Technology for collecting, processing, storing, transmitting, and understanding intelligence information is improving dramatically. National priorities and resource allocations are shifting to meet social environmental and economic demands. In addition, there is an explosive increase worldwide in data and information available to those capable of accessing it.To cope with this tremendous change and to prepare for the rigorous demands of the coming new millennium, the intelligence enterprise
itself must change. The product of the intelligence enterprise is information providing knowledge needed by its consumers. Knowledge-based information is information expressed in the context and format which enables its rapid assimilation by the consumer in a timely manner to contribute meaningfully to the decisions the consumer is facing. More than ever, in the new international environment, information, and the knowledge it provides, will continue to be critical core resources of the Intelligence Community vitally needed for our national security and prosperity.While the Community has functioned admirably in the past and is constantly improving, changes are occurring so rapidly and dramatically that a coordinated, enterprise strategy is needed to cope with rapid change and move forward. We must provide knowledge-based
solutions to our customers, not merely information products. We must identify and adopt new business models and practices that will help assure our continued success in serving intelligence consumers and our nation. We must work more closely together, sharing information and expertise as an agile, collaborative enterprise.Although information technology will both enable and drive substantial changes within the Intelligence Community in decades ahead, the challenge before us is not merely a technical challenge. It is also a significant cultural challenge. The Intelligence Community must evolve a culture appropriate for the dynamic environment of the 21
st Century: re-engineering business processes to accommodate new modes of operating with our customers and amongst ourselves; establishing organizational motivations and individual professional incentives to ensure the success of these innovations; and, rededicating ourselves to achieving customer satisfaction and to meeting our customers' varying intelligence needs as quickly and effectively as possible. Working together, we can realize a future of greater cooperation, closer collaboration, and healthy competition to produce the best intelligence for the nation at the lowest total cost. Above all, we must remind ourselves of the paramount importance of continuing our success in fulfilling the Community's total intelligence mission and the fundamental importance of resource sharing and prudent management in maintaining that success. Finally, we must prepare ourselves to flourish as a more agile intelligence enterprise in the 21st Century.
Our Challenge...
To build greater focus, direction, and responsiveness into U.S. intelligence activities, the President last year signed a
Presidential Decision Directive (PDD) on intelligence priorities. PDD-35 established for the first time a categorization of intelligence needs. PDD-35 is a flexible document designed to accommodate shifting priorities within the categories. Current Presidential priorities cover a diverse spectrum of direct and potential threats to U.S. national security interests. The target priorities established in PDD-35 will change as the world situation changes. To be adequately responsive to these challenges, the Intelligence Community must sustain a global coverage capability in addition to concentrating resources on priority hard targets.Useful intelligence information provides national security, law enforcement and other policy making officials with crucial knowledge that can produce a strategic advantage over our adversaries. Intelligence can even provide insight to knowledge about what knowledge the adversary has regarding our own plans and capabilities. The need for intelligence information in the 21
st Century will be greater than ever. It must be managed effectively and efficiently and protected. We face the challenges posed by an increasingly diversified and uncertain threat during a period of declining resources. Only through enterprise integration and prudent management of intelligence information (our core resource) can we meet these challenges successfully.Though many in the Community recognize the need for and potential value of a worldwide virtual intelligence environment capable of efficiently and dynamically exploiting the rich information resources of the Intelligence Community; and though many are aware of the powerful potential capabilities offered by information technologies to be available at the dawn of the 21st Century; not all have acknowledged and made the commitment implied by the necessity of evolving separate components of the Community to an integrated enterprise capable of realizing the potential and capitalizing on the opportunities emerging.
Managing Information to Support Our Missions...
Characterizations of the missions and functions performed by the Intelligence Community vary. Four principal missions have been identified and will be addressed in this discussion. In reality, these missions often overlap, and include common areas of information interests. The four Intelligence Community missions, as stated by the former Director of Central Intelligence, are: to provide intelligence support to national level policymakers, provide intelligence support to military planning and operations, provide intelligence support to law enforcement, and counter foreign intelligence activities.
Their wide diversity demands an equally wide diversity of adaptive intelligence processes, sources, and methods. The complexity of today's world and the interaction among nations and subcultures make it imperative that we adopt a flexible network of intelligence information collection, analysis, retrieval, and reporting. The nation can- not afford to trap potentially critical intelligence information and knowledge in narrowly defined organizational channels. The response times needed for decisive action are becoming too short, and the potential relevance of information collected in one mission area to other mission areas is too great not to be effectively and efficiently shared across the intelligence enterprise.
"The United States intelligence effort shall provide the President and the National Security Council with the necessary information on which to base decisions concerning the conduct and development of foreign, defense, and economic policy and the protection of the United States national interests from foreign security threats. Specifically, the missions of U.S. intelligence are to:
• provide intelligence support to national level policymakers,
• provide intelligence support to military planning and operations,
• provide intelligence support to law enforcement, and
• counter foreign intelligence activities."
John Deutch, Former Director of Central Intelligence
National Performance Review
; 1996
Support to National Policymakers
As a group, senior policymakers are exceptionally busy people. In the Executive Branch, policymakers at the Presidential and Cabinet levels use intelligence to support decisions involving a wide range of national security and other matters. The President's
National Security Strategy describes the scope and breadth of intelligence expected by policymakers.Economic intelligence will play an increasingly important role in helping policymakers understand trends, threats to U.S. economic interests from foreign intelligence entities, and unfair trading practices. Intelligence must also identify emerging threats that could affect the international economy and the stability of nation states, such as the upsurge in international organized crime and illegal trafficking in narcotics.
The development and implementation of policies to promote democracy abroad rely on sound intelligence support. In order to adequately forecast dangers to democracy abroad, the Intelligence Community and the policymakers it supports must track political, economic, environmental, social, proliferation and other military developments in those parts of the world where our interests are most heavily engaged and where collection of information from open sources is inadequate. This contributes to early warning of potential crises and facilitates preventive diplomacy.
Congressional legislators also benefit from intelligence gathered in support of the above priorities and use it in formulating national legislation, influencing the execution of foreign policy, and structuring the national defense. In some circumstances, our intelligence is shared with policymakers at international organizations when such sharing is consistent with our national objectives.
The implications of the broad range of intelligence information needed to support policymakers place a premium on the ability to look within and across national boundaries at any given region in the world, and to select and integrate information needed to capture the situation at a level of depth and trust sufficient to support prudent decision making. Extensive and rapid cross-community collaboration and all source information fusion are critical.
Although policymakers require access to many forms of intelligence, there are some key considerations regarding information content and structure, availability, timeliness, and presentation. policymakers generally prefer all-source products to ensure credibility and a balanced perspective. Information must be presented in context with the issues of daily concern, and it must be accurate, in a form easily understood, and conveniently available when and where desired. Finally, presentation format needs vary as a function of personal preference. Some individuals prefer personal briefings, others read specialized products and others routinely browse through Intelink-sources.
Support to Military Planning and Operations
As we approach the 21
st Century, we must be prepared to meet many kinds of challenges, in military operations throughout the world. We may be required to wage war on more than one continent simultaneously. Today, the world is no less turbulent or dangerous than it was during the Cold War. Myriad regional threats, low-technology adversaries with nuclear, biological, or chemical weapons, and the ever-present specter of large-scale terrorism clearly demonstrate the need for us to maintain a globally engaged military force. Given America's global interests and role as a superpower, our military has little choice but to maintain the capability to respond across the full spectrum of potential crises.Even in peacetime, our forces engage in many activities vital to our security, some of which place unique and stressing demands on our intelligence capabilities. Detecting the development, testing, and use of advanced weapons and covert activities throughout the world is a vital, day-in, day-out activity that requires highly sensitive, adaptive, and responsive intelligence capabilities, information, and information services.

As stated in the recent
Annual Defense Report and Quadrennial Defense Review:• "The United States must be prepared for a wide range of contingency operations in support of U.S. interests. These operations include, among others, smaller-scale combat operations, multilateral peace operations, non-combatant evacuations, and humanitarian and disaster-relief operations.
• U.S. forces must be forward deployed or stationed in key overseas regions in peacetime to deter aggression,
• U.S. forces must be able to offset the military power of regional states with interests opposed to those of the United States and its allies. To do this, the United States must be able to credibly deter, and, if required, decisively defeat aggression, in concert with regional allies, by projecting and sustaining U.S. power in two nearly simultaneous major regional conflicts (MRCs)."
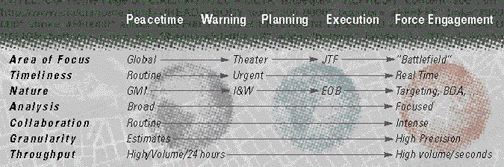
As indicated by the figure above, as the disparate nature of military engagements varies widely across the crisis spectrum, the nature of intelligence information required varies markedly in area coverage, timeliness, resolution, context, presentation, and other parameters. What may not be so obvious are the somewhat dramatic shifts in the nature of intelligence information demands as a particular crisis progresses from one stage to another.
Support to Law Enforcement
The Intelligence Community provides information to support law enforcement,
particularly concerning transnational activities that threaten U.S. interests.
Chief among these activities are terrorism, narcotics trafficking, proliferation
of weapons
of mass destruction, and international organized crime.
Intelligence regarding these and related areas of concern is needed to support
diplomatic activities, to support international and domestic law enforcement
efforts to prevent and prosecute illicit transnational activities, to assist
foreign nations in controlling such activities within their borders, and,
occasionally, to form the basis for appropriate military actions. Intelligence
is also provided to criminal justice and regulatory agencies regarding foreign
personnel or organizations located within our borders that are the subject of
criminal investigation.
Terrorists, whether from well-organized groups or more loosely-organized groups, such as the one responsible for the World Trade Center bombing, have the advantage of being able to take the initiative in the timing and choice of targets. Countering terrorist activities requires, in particular, the coordinated efforts of the Departments of State, Justice and Defense, the FBI and the CIA. The coordination strategy must focus on the effective, timely integration of intelligence information, diplomatic and rule-of-law activities, and close cooperation with other governments and international counter-terrorist organizations.
Our counter-narcotics strategy has shifted from the past emphasis on transit interdiction to a more evenly balanced effort with source countries to build institutions, destroy trafficking organizations, and stop supplies of illicit drugs. We have also undertaken initiatives to reinforce interdiction activities near the source of production. When one examines the various counter-narcotics scenarios that we support, the critical need for information agility and close Community collaboration becomes apparent. The demand for diverse types and media of information, contextual integration, multi-agency collaboration, time sensitivities, resolution required, and other information-support characteristics varies dramatically from scenario to scenario. And multiple operations can and do occur simultaneously
.International criminal enterprises are presently moving vast sums of illegal gains through the international financial system with impunity. Our strategy to counter international organized crime focuses on undercutting the financial underpinnings of criminal enterprises, specifically, combating money laundering throughout the globe. This requires timely knowledge-based information products and services related to these illegal activities.
Finally, we seek to prevent additional countries from acquiring chemical, biological and nuclear weapons and the means to deliver them, and will use the full range of our intelligence capabilities to detect such activities. However, should such efforts fail, our forces must be prepared to deter, prevent and defend against their use. The United States is placing a high priority on improving the ability to locate, identify, and disable arsenals of weapons of mass destruction, production and storage facilities for such weapons, and their delivery systems. This requires knowledge obtainable from analysis of information from a wide variety of sources.
Law enforcement personnel prefer information products of immediate value providing knowledge regarding on-going investigations. The intelligence information must be accurate, easily understood, and sanitized to an unclassified level, if possible, to minimize obstacles presented by information handling and disclosure requirements. Intelligence information must also be conveniently available when and where desired-it must easily accommodate the rapid-reactive nature of criminal investigations.
Support to Counter Foreign Intelligence Activities
Today, foreign countries are shifting the focus of their efforts to acquire sensitive information regarding U.S. capabilities from the traditional defense-related efforts characteristic of the Cold War. This is leading to expanded, focused attacks on economic and technological information associated with terrorism and related hostile information operations in the modern era. Some of these countries have been considered ideological and military adversaries for decades. Their targeting of our economic and technological information is not new but has continued and expanded. Others are either longtime allies of the United States or have traditionally been neutral. Elements of apparently friendly countries may target our economic and technological information despite their generally friendly posture. In some cases, they may take advantage of their legitimate access to our facilities and collect sensitive information more easily than our military adversaries. Some countries have infrastructures that allow them to easily exploit high-tech information and use it to compete against our commercial firms. Adversaries seldom use one method in isolation but combine them into concerted collection programs. These collection programs encompass traditional espionage methods primarily reserved for collecting national defense information as well as other methods typical of industrial espionage, including tasking foreign students studying in our universities, debriefing foreign visitors, making contacts during international conferences and Trade Fairs, and accessing commercial databases.
Counter intelligence is an observation-driven process-interdiction involves rapidly reacting to data regarding organizations, people, the activities that bring them together, and the locations and environments within which the activities occur. Thus, counter intelligence personnel must have information from many diverse sources that can be readily searched and accessed, even though they cannot predict which data item (the search basis) may be the most important at a given time.
Potential Mission-Support Scenarios of the Future
During a period of heightened world tensions, Ray receives an emergency alert from intelligent intrusion-detection software agents about an attack from cyberspace on an important database providing critical intelligence to deployed U.S. and coalition forces. He and his emergency response colleagues at the other affected locations immediately begin a desktop video conference to share information about the attack, review damage assessments, and formulate a recovery plan.
Meanwhile, after identifying the site's firewall as the point of attack, the agents automatically reconfigure the firewall to cut off the attacker's access and report back to the emergency response team. An attack profile analysis agent is then launched to analyze the nature of the attack and determine who the perpetrator might be based on electronic "fingerprint" evidence left behind...
Bob was asleep when the call came from Kathy. The instructions were brief and to the point. "Find out all you can about the current refugee status in Zawalu." Bob starts to work. Bob loves working-because Bob isn't human. Bob is a piece of intelligent software called an agent.
Because of the general nature of the request, Bob calls an information mediator, another software agent that knows where the right information might be. The mediator then launches a series of multimedia search agents to search appropriate databases and work with specific search engines, performing semantic and syntactic translations as necessary. As results come in, Bob filters out information that he knows is duplicative or tangential. He employs the latest analytical tools to corrrelate the information and present it in a form that Kathy can readily understand, highlighting patterns and relationships in the information that she might otherwise overlook. Bob then goes dormant awaiting Kathy's next request...
Maj. Thomas is monitoring the demilitarized zone border between North and South Ranolea. Due to recent reports indicating a sudden increase in civilian refugee flow, he decides to task open source and national assets for a current imagery scan of the entire border. The resulting imagery contains a large suspicious object that he can't identify.
He launches several automated directory service agents to locate analysts who can participate in an immediate telepresence conference. Very soon he is "seated" at a virtual conference table with Capt.Clark and Maj. Masters, acknowledged experts in the field. The group, who appear to be in the same room together, view the object simultaneously on the shared, high-resolution, large-screen whiteboard. Maj. Masters says it looks like massive tents constructed for shelter after a devastating tidal wave a few years ago in Galdelor. As a result, Maj. Thomas modifies his tasking to take another look...
Irena has been monitoring Gulebonia for seven long years. Because Gulebonia is considered a low intelligence priority, few resources are devoted to its coverage. However, Irena continues to monitor it along with several other higher priority areas because her agency is aware that in the current unpredictable world climate, Gulebonia could quickly become tomorrow's problem. She is assisted in this task by a dozen or more constantly active software search agents whose job it is to work in the background building standardized country files.
Suddenly, with an invasion of the Syrinoco Embassy by Gulebonian
revolutionary terrorists and the taking of over 100 foreign hostages,
international interest in Gulebonia explodes. Irena joins a crisis team
consisting of experts from across the Community. The information she has
collected and the knowledge she has gained over the years, along with her
network of contacts, significantly contribute
to the team's work. The U.S.
initiates a plan for direct support to Gulebonian government...
Additional Challenge of a Dynamic Environment...
"We find that the vast majority of people who work in the IC are extremely dedicated to their work and to its value to our national security. The system within which they work, however, is not designed to get the very best out of them in terms of either bureaucratic rules or the type of leadership (rather than management) that breeds lean. Curiously, the IC tends to manage personnel much like it manages collection, through an array of 'stovepipes' that are bundled together but are not well inter-connected."
House Permanent Select Committee
on Intelligence: IC21
"It is the sense of Congress that, during the next five-year period beginning with 1996, executive agencies should achieve each year at least a 5 percent decrease in the cost (in constant fiscal year 1996 dollars) that is incurred by the agency for operating and maintaining information technology, and each year a 5 percent increase in the efficiency of the agency operations, by reason of improvements in information resources management by the agency."
Clinger-Cohen Act of 1996
It is clear that the Congress holds great faith in the utility of information technology in achieving overall improvements in Federal programs. It also recognizes the value of digital networking and collaborative technologies in supporting electronic commerce and other Government functions overall. The ever-increasing importance of the role of information management in the operations of the agencies has been recognized across the Federal Government. Recent legislation has established a pilot approach to creating, implementing, and assessing the value of information and the challenges associated with managing information resources. The Intelligence Community is pursuing a similar experimental and collaborative approach as we collectively learn how to become more effective managers of our information, information services, information systems, and related resources.
As we near the beginning of the 21
st Century, the Intelligence Community is faced with an additional information management challenge in the form of a rapidly changing environment. The Community must be aware of the changes taking place and, as an integrated enterprise, devise an adaptive strategy for coping and moving ahead with agility. Six major categories of change that impact on the Intelligence Community are outlined below.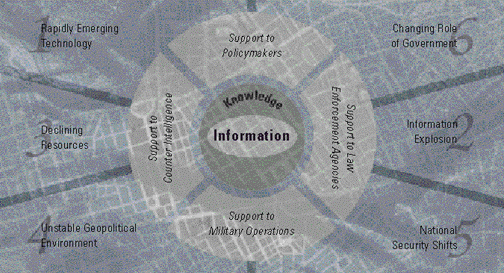
Rapidly Emerging Technology
It is no secret that we are in the midst of an information revolution with respect to technology that can better enable us to achieve dynamic information management and exploitation capabilities. Opportunities are growing for expanded communications "bandwidth" capacity "on demand," and increased efficiency through technologies such as asynchronous transfer mode (ATM). Open networking capabilities are providing us with more flexibility and diversity. Commercial off-the-shelf security protection products and services are emerging that warrant consideration for intelligence intranet applications. And, the rapid evolution of the Internet and its worldwide popularity are spawning commercial, web-based information access, processing, dissemination, and collaboration capabilities at astronomical rates.
But, if we don't share with each other our experiences with new technology, we increase the risk of imbalanced capability and interoperability hurdles across the Community. If we don't execute smart acquisition practices that enable us to insert new technology into our developmental programs or fielded systems cost-effectively as it emerges, we may not be able to exploit those opportunities effectively.Information Explosion
New information repositories are cropping up all over the globe every day. New-found "easy access" and competition are motivating providers to make more and more information available to authorized users. Like new technology, this is potentially very good news
- but, only if we are aware of the information available and where it can be found. If we aren't equipped with the insights, tools, and capabilities that will help us rapidly find and integrate what we need into the context and presentation that contributes knowledge supporting decisions and actions of our customers, then we run a significant risk of drowning them in a sea of data and information glut. Conversely, if we can't know what we need to know because of risk avoidance practices that inadvertently prevent our principal customers from having an awareness of or accessing information that is critical to their mission, then we've wasted valuable resources. Tradeoffs between providing access to information and protecting it increasingly dictate a risk management policy with applicable tools and implementation strategies to implement that policy.Declining Resources
The reality of steadily decreasing budgets, staff downsizing, and facility shutdowns and consolidations is a way of life we are all too familiar with. "Doing more with less" is probably a part of more corporate vision statements than any other phrase. New technology and better infrastructure capabilities and tools certainly will help us do the things we've always done a bit more expediently; however, unless we realize that we are all components of a common enterprise, with complementary skills and products, then we will not gain the truly appreciable benefits and economies available through an integrated information infrastructure space. Unless we carefully examine and re-engineer our fundamental business processes in context with increased Community collaboration through enabling technologies, our mission customers will surely suffer the impact.
Unstable Geopolitical Environment
The world today is characterized by much uncertainty with respect to potential threats to our national security. Acts of terrorism are no longer restricted to foreign soil, and those organizations and individuals who pose this type of threat are extremely difficult to identify in advance. Maneuverable targets present a formidable challenge to our ability to locate, identify, and predict. If our Intelligence information management capabilities do not adequately cover future contingencies (including terrorism and hostile information operations), and if they are not agile and quickly adaptive to new, unpredicted situations, then our ability to respond to unforeseen circumstances and threats to our security will be at risk.
National Security Shifts
Since the end of the Cold War, our nation has been adapting its security strategies and policies to meet new and emerging threats, growing partnerships with free-world allies, and opportunities to help spread democracy and to provide humanitarian assistance where the needs arise. The ability to be responsive depends heavily on the timely and agile support of the Intelligence Community. Success also depends on our ability to collaborate not only within our own Community, but also with DoD, other Federal institutions and those of foreign nations. Without prudent and adaptive risk management policies and practices in place, we run the risk of either blocking critical information access to our Community partners, or, conversely, we increase the risk of providing sensitive information to today's friends who are potentially tomorrow's foes.
The Changing Role of Government
The Federal legislative and regulatory environment has changed significantly over the past few years in several areas that impact information management and information technology application in the agencies of the Federal Government.
Taken collectively, it is evident that Congress is genuinely concerned about the overall efficiency and effectiveness of the Federal Government, and that Congress believes that an effective process of information resources and technology management can contribute significantly to improving Federal programs. While much of the specifics of the legislation are focused on managing information technology and the acquisition process, the term "information resources" is broadly defined to include
information and related resources (such as personnel, equipment, funds, and information technology). Congress has clearly established the fundamental principle of managing information as a "corporate" resource of agencies of the Federal Government. The various legislation emphasizes the integrated management of all information resources (including information technology, information systems and related resources). Legislation is less definitive about processes for managing and sharing information itself, leaving individual agencies to be accountable for prudent management decisions based on clearly defined objectives.The legislation does establish some common objectives for information management across the Federal Government. These include establishing personal accountability for achieving Government program results, adopting common best practices, using commercial technology wherever feasible, and integrating agency business strategic plans with agency performance improvements, program budgets, information technology plans, and information infrastructure architectures. Selected aspects of relevant recent legislation are highlighted below:
The Government Performance and Results Act of
1993 (GPRA) was enacted to address waste and inefficiency in Federal programs, primarily due to insufficient specification of program goals, inadequate information on program performance,The Federal Acquisition Streamlining Act of
1994 (FASA) was enacted to revise and streamline the acquisition laws of the Federal Government. Among its many provisions, it seeks to improve overall Government efficiency in acquiring information technology and information systems as well as applying modern information technology to the entire Federal acquisition process. FASA emphasizes a strong preference across the Government for buying commercial-off-the-shelf (COTS) items, rather than contracting for unique development of components.The Paperwork Reduction Act of 1995 (PRA) was enacted to make Federal agencies more responsible and publicly accountable for reducing the burden of Federal paperwork on the public. While the focus of the PRA is on public information and record keeping, the goals and principles of information resources management clearly apply to the information-related activities of Intelligence Community component organizations.
The Information Technology Management Reform Act of
1996 (ITMRA), also known as the Clinger-Cohen Act, emphasizes that the process for acquisition of information technology should be a simplified, clear, and understandable one that specifically addresses the management of risk, incremental acquisitions, and the need to incorporate commercial information technology in a timely manner. Executive agencies are expected to implement a process for maximizing the value and assessing and managing the risks of its information technology acquisitions. The Clinger-Cohen Act also establishes the position of Chief Information Officer (CIO) as the senior information resources management official in each organization. Most of the management principles of this legislation are applicable to the Intelligence Community.
Turning a Challenge Into an Opportunity...
We are living in an age where information, and the knowledge derived from it, is becoming vital to the successful conduct of our daily affairs, from the most mundane to the most critical. Information has become integral to all activities. In the factory, the office, and the home, information technology is the key to making better decisions and getting results. In this information age in which we live, the power of information multiplies the effect of all other resources. Industries and nations are seizing the opportunities offered by information management and information technology to become more competitive in the global environment. Information must, therefore, be recognized as the core critical resource of the Intelligence Community, a resource which we must manage prudently.
The advent of hypertext-linked "web" technology combined with the global network of networks known as the Internet have made a wide variety of multimedia information available. Users all over the world have almost instant access to a great variety of widely distributed information. This technology, providing access to enormous quantities of data and information, has been incorporated into and supports the business process of the Intelligence Community. Whether we will be overloaded by information or will control the information to provide knowledge needed for strategic and tactical advantage depends on development of sound information management practices and capabilities.
Intelligence consumers throughout the world continue to face new, increasingly complex and short-fused challenges. The Intelligence Community's ability to respond to these challenges, shoulder to shoulder with those consumers, requires a commitment to understand them. We must acquire all information available that contributes the knowledge they need to support effective decisions and we must deliver that properly formatted information on time and in the context of those decisions. But in doing this, we must maintain an adaptive posture and strategy enabling us to rapidly detect and respond to unforeseen challenges ahead. In short, our challenge is to seize the opportunity to become a more agile enterprise.
Becoming a More Agile Enterprise...
"The agile enterprise provides solutions to its customers, not just products. It works adaptively, responding to marketplace opportunities by reconfiguring its organization of work, its exploitation of technology, its use of alliances. It engages in intensive collaboration within the company, pulling together all of the resources that are necessary to produce profitable products and services regardless of where they may be distributed. And it forms alliances with suppliers, with customers, and with partnering companies. And finally it is a knowledge-driven enterprise. The agile company is centered on people and information, not on technology alone, on people using technology in creative ways."
Agile Competitors and Virtual Organizations
, 1995"Intelligence is a scarce resource... Demand consistently outstrips supply. In the industrial world, the two approaches that have evolved to cope with this challenge are top-down central planning and bottom-up consumer-driven free markets...The waste and inefficiency of central planning can no longer be tolerated. Cost-effective intelligence support under the National Security Strategy of Engagement and Enlargement requires the resiliency and the discipline of the marketplace...Classical economic theory says that consumers would buy those products that give them what they need for the least cost. The concept of intelligence 'value' is born. Intelligence consumers could buy products off the shelf or have them tailor made. Inefficient producers would eventually be forced to improve or leave the market."
Todd Brethauer, Adam Smith
Examine the Intelligence
Economy
Studies in Intelligence
,
Out of a concern for the competitiveness of U.S. manufacturing in the global market, in 1991 the DoD commissioned a report,
21st Century Manufacturing Enterprise (Iacocca Institute), authored by Steven Goldman and Kenny Preiss of Lehigh University. The report described the concept of an agile enterprise, a key feature of which was the ability of an industry to fragment itself into smaller, leaner, more flexible groups of specialists that would be able to reconfigure on demand to meet market needs and global competitive challenges.The agile enterprise concept is based on the precept that business processes and procedures should serve the enterprise, and not the reverse. In order to remain competitive and viable in an increasingly competitive global environment, it is imperative for businesses (and intelligence organizations) to understand that they need to operate efficiently and effectively, providing their customer base with the products and services they need to carry out their missions and functions. A successful enterprise takes advantage of what the commercial marketplace has to offer. Those organizations that don't collaborate and don't form alliances may find themselves increasingly isolated. As intelligence organizations, we must also collaborate and interoperate across the broad spectrum of the larger Intelligence Community in order to provide the best information products and services on time, at the best price.
The agile enterprise concept is easily adaptable to the Intelligence Community. Just as the agile enterprise focuses on smaller, complementary, and reconfigurable areas of manufacturing expertise, the agile intelligence enterprise focuses on a high degree of collaboration across components of the Intelligence Community to produce knowledge products. The ability to "reconfigure" on demand to meet the needs of customers involves not only agility in adapting community roles and alliances "on the spot" to meet current needs, but also agility in reconfiguring, interrelating, and integrating information resources of the Community to provide the knowledge needed by those customers
The more agile intelligence enterprise envisioned for the future, will manage information as a critical corporate resource and is readily share it across the enterprise and with its customers. If the Community cannot provide the right information to the right people at the right time and in useful form and context, our customers will suffer and be forced to seek other sources to obtain the knowledge required for their decisions and actions. In fact, with the breathtaking growth of the Internet and the quantity and quality of open source information becoming available, intelligence consumers are exploring these resources directly, as well as our products. It is not a coincidence that CNN is a ubiquitous fixture in many intelligence watch facilities and operations centers.
The Joint Staff's Joint Vision 2010 describes the need for "information superiority," defined as "the capability to collect, process, and disseminate an uninterrupted flow of information while exploiting or denying an adversary's ability to do the same." The need for information superiority is vital to our nation. An efficient and cost-effective way to ensure that we provide superior information will evolve from a more agile enterprise centered on skilled knowledge workers and collaboration as an information "marketplace," where intelligence suppliers and customers conduct the exchange of information products and services. Customers require timely and accurate information; suppliers require feedback on the knowledge that customers need so that high quality information contributing to that knowledge can be provided in the most efficient, cost-effective, and trustworthy manner.
Where appropriate, competition among information providers must be encouraged as a means of continually improving information resources and services. Value-added providers who do not keep their services up to date and relevant to customers needs, or who do not form strategic and ad-hoc collaborative alliances, may find their business eroding over time, as customers move on to other, more efficient and responsive, sources of information and services. Provider cooperatives who are meeting customers' needs will naturally want to continue to invest in improved information sources, technology, and expertise that provide mutual benefit as they adapt their business or functional processes to capitalize on and exploit these improved resources.
The "information marketplace" must not become a "free market" without constraints, controls, or cooperation. Common information will be needed by all, and provided from common sources. Furthermore, cooperative planning and funding (or "subsidizing") is necessary to ensure that adequate global coverage is applied to potential "hot spots," not just focusing on those areas that are current "best sellers."
An information marketplace is not a system. It is a perspective or framework for thinking about our information resources and discovering the expertise, tools, techniques, policies, and procedures for managing these resources. To establish and maintain a healthy and productive marketplace we must expedite progress in establishing a shared electronic intelligence information space that builds upon and expands beyond the current Intelink environment. Viewing this emerging environment as an intelligence information marketplace in concept can be helpful as we rapidly evolve toward a more agile intelligence enterprise.
Consistent with the information marketplace concept, the vision of a more agile intelligence enterprise of the 21
st Century is based on an open enterprise-wide culture of collaboration and information sharing. It assumes policies, practices, and incentives that will foster that vision, along with the supporting information technologies and communications infrastructure needed to make it a reality.Joint Vision 2010 makes this very point: "...The unqualified importance of information will not change in 2010. What will differ is the increased access to information and improvements in the speed and accuracy of prioritizing and transferring data brought about by advances in technology. While the friction and fog of war can never be eliminated, new technology promises to mitigate their impact."
Information management does not necessarily imply having access to more information; to the contrary, it frequently means providing
less but the right information that provides the knowledge needed by the customer. It also means having superior tools to manage that information. Information management is a term that can be applied broadly or narrowly. In the broadest sense, information management includes the full set of issues surrounding the timely acquisition, processing, organization, and presentation of information needed by customers at all levels in support of the mission at hand. While the focus of information management is on the people, missions, quality, accuracy, timeliness, and utility of the information being managed, the underlying information technology can help enable it to work effectively and efficiently.The tools and technologies needed for acquiring, analyzing, manipulating, storing, searching, retrieving, transmitting, and publishing information are increasing in speed and capacity, and steadily decreasing in cost. Available communications bandwidth of fiber and wireless systems is dramatically improving the ability to rapidly share information among analysts and processing facilities. Networking technologies are rapidly emerging, making it easier for us to access Community and other information regardless of location.
Nevertheless, even with the expanding potential that technology provides to shower intelligence consumers with information, that must not be our goal. Instead, we must develop and apply information management principles, policies, techniques, and procedures to reduce the volume and increase the timeliness and quality of knowledge-based information delivered. A set of principles to guide it on the proper course are proposed below in Table 2.

Enabling Components of an Agile Enterprise...
Agility across an enterprise depends upon closely interrelated and synchronized components: distributed collaborative processes, a common telecommunications infrastructure, shared information service capabilities, and an integrated information space. Each of these is a critical dimension or facet of an agile enterprise, and all are intimately interrelated and dependent upon each other.

Distributed Collaboration
A major step toward exploiting information as an enterprise is overcoming barriers related to a combination of policy and regulations (not always easy to change), business practices ("but we've always done it this way",) and, most importantly, culture. This isn't just a matter for debate among managers and policymakers. The entire enterprise workforce, including technology and knowledge workers, is an integral part of the equation. Culture influences policy and policy reflects the culture, and both of these can make it difficult to implement optimal technical solutions.
In addition to modifying policies and procedures over time, positive mechanisms are needed to promote information sharing across the Community, on an individual and on an organizational level. In the traditional environment the tendency is for an organization to focus on direct support to a specific customer base. Information sharing is often viewed as a serendipitous occurrence, not something explicitly planned. Therefore, many times this sharing is awkward or technically hard to achieve and goes awry. Further, there may be no incentive for information providers to make their products known to other potential customers and all the work falls on the customer to search for and pull information from potentially useful sources. Thus, a new paradigm for rewarding organizations for populating the information space (or stocking the marketplace) needs to be instituted.
Policies that have been in place for many years need to be reevaluated to determine whether they help or hinder information sharing and collaborating. Some policies are legally binding statutes that cannot be easily changed. Others are procedural. Still others are both cultural and rooted in the technology or paradigms of the past. One such example is the entire area of security policies. Recent movements toward risk management versus risk avoidance will help us achieve greater information sharing and interoperability, but create vulnerabilities that may not be clearly understood. How best to strike a balance in these policies is a difficult issue that must be resolved in ways suppliers and customers understand and endorse.
Information Service Capabilities
Central to the vision of the 21
st Century is the collaboration and information sharing that will take place among members of the intelligence enterprise and with its customers. Though individual components of the enterprise and its customers may be collocated in the same building or separated by continents, they will have at their disposal a variety of tools and capabilities that ensure they have the right information at the right time in the right form for their purposes. Along with the underlying communications infrastructure that ties it all together these tools and capabilities include:•
Publishing and dissemination tools for placing knowledge products into the information space and distributing them to users needing them• Sophisticated semantic multimedia
searching and accessing tools that work across the broader information space for precision recall of information and expertise• Presentation and manipulation tools that allow the information to be conveyed and presented to, or
analyzed by, customers in the most effective way•
Collaboration tools for communicating, working and sharing information with others• Directories for
locating information resources, people, organizations, and services across the enterprise ("white pages" and "yellow pages")• An unobtrusive and flexible security infrastructure to ensure the availability and integrity of the information in the information space and to
protect the information from unauthorized access or tampering, and to limit access toThough we already have many of these to some degree, the rapid pace of technology development is enabling improvements both in terms of robustness and functionality. As opportunities arise, we must reexamine the way we do business, both within individual organizations and across the enterprise, making adjustments as necessary to ensure that new capabilities are exploited to their best advantage. We must also be constantly alert for new technologies that have the potential to alter our processes significantly and exploit opportunities for improving the way we support our missions.
Publishing and Disseminating Information to Customers
As we move forward to build and manage an integrated electronic information space, we must reexamine the meaning of publishing, especially in the context of a web-based environment. In the paper-publishing world of the past, the act of publishing clearly began when the author delivered a manuscript to a publisher for design, composition, editing, typesetting and printing. Although we still talk about an explicit "publishing" process in the electronic world, lines are beginning to blur, and what we think of as a finished "product" is beginning to change.
We are now in what we might term a "webified" paper product phase. Our products are electronic and on the Web, but still mimic the paper product model. Typically these are formal products whose structures lend themselves to serial presentation, are fairly static, and still largely text based. Users accessing this information see it in the state at the time it was published. To see an update, users must explicitly access the updated product. And, because one of the biggest responsibilities that publishers have is to ensure that their information can be easily retrieved and evaluated by customers, publishers and authors must manually add tags and metadata to their products. These tags are used by search engines to find the information requested, by security tools to make access control determinations, and by users to evaluate whether a product is suitable for their purposes.
In the future, we must devise better ways to dynamically link and present information electronically located at diverse sites across the information space. Automated tools are expected to help in linking, organizing and presenting information. Also, tools such as sophisticated automated foreign language translators will be needed to present information to the user in the language of choice. Products will be more dynamic and tailorable, guaranteeing that users will always have access to the latest information. Already, tools to automatically tag products for content and format are coming into use, with the expectation that these will be replaced by even more powerful semantic tools that can rapidly search on complex concepts and contexts.
Publishing information into the information space is the first step in disseminating it to the users who will then "pull" it directly, or receive it as a result of automated profile selection or from providers that explicitly "push" it to them.
Today, information "pull" is largely accomplished through browsers or search engines with varying degrees of precision. Browsing or searching is a more informal process and whether or not a user finds what he or she is looking for depends on how well the information is organized and linked. Information "push," on the other hand, is currently accomplished through text-based electronic mail, messaging, or multimedia, large distribution, unidirectional broadcast. In the future, more automated and less intrusive push capabilities are expected to be available, with sophisticated multimedia profiling, resulting in efficient delivery of more complete information products. The entire concept of electronic publishing must be redefined to reflect these rapidly evolving capabilities. A major obstacle may be cultural factors, as products lose authors identities and associations.
Searching and Accessing Information
Where information was once largely organized in physical libraries and limited online collections, it is now increasingly available in digital form and distributed across large multicommunity networks. Probably the most frequent complaints users have regarding large electronic repositories is that they either can't find the information they are looking for, or they get too much information. In our business, we have another complication-often users don't know when needed information exists, or is in an environment to which they don't have access due to security constraints or lack of connectivity. The best information in the world is of little value if the users cannot find and access what they need when they need it and in a form that they can rapidly understand and use.
Current information retrieval tools are largely keyword-based. Users generate natural language or boolean queries describing needed information, and documents are retrieved based on how well they match the user's query (often requiring the recipient to plow through reams of words to find the "nugget" sought). More recently, concept or semantic search capabilities have been incorporated into retrieval technology to help remove some of the burden placed on users to identify all the useful search terms, as well as having to understand how they might be used in actual documents. While text search is relatively mature, non-textual searching is more problematic. Searching audio, images, and video is much more difficult even for the simplest queries. In the future, new technologies for searching video, images, and audio information directly are expected to augment the text search technologies of today.
Global access to information has increased the need to handle documents in multiple languages. Today users who need access to information published in languages other than their own must use relatively primitive multilingual retrieval tools, crude machine translation tools, or costly manual translation services. While finding a Russian or Chinese linguist over the years may not have been a problem, as we enter an increasingly volatile political world order, the availability of people able to translate obscure third world languages is less certain. This becomes an even greater problem if they need to have security clearances.
A more agile intelligence enterprise will need a "deep" semantic retrieval capability that will enable users to state their requirements in a natural way (natural language, images, vocalizations) and, given the context of their particular mission or assignment, be presented with the precise information they need. The mechanism for performing this search might be an autonomous intelligent agent that can fully negotiate for information to match the user's information needs. These agents should be able to spawn other, more specialized agents, such as security agents, that can collaborate amongst themselves and with each other in carrying out an assignment. Security agents, for example, would negotiate access to information objects and services. Such software agents should be capable of filtering out information that might be less useful, even if it were directed toward the user (e.g., a "junk mail" filter). Finally, these agents should be capable of learning and adapting to the user's work patterns, predicting his needs based on knowledge about hot topics in the information space, and alerting him to activities or products that might be of interest.
Analyzing Information
Even if succinct, precise information is delivered to a user in an acceptable form, oftentimes the user needs to further manipulate or process the information to a more useful form. Tools for classifying, analyzing, summarizing, synthesizing, and visualizing information are becoming increasingly important to the end user (customer) and analyst alike.
These tools can help identify patterns and organize the information into classes and groups to find relevant relationships. Profiles are an example of how patterns of interest (such as keywords and phrases) can be recognized in information today. But users won't always know what patterns to look for, or that there are even any patterns at all in the information. Exploratory data tools can help make sense of seemingly disparate data and suggest patterns or clusters. Today's tools are fairly rudimentary and usually aimed at quantitative data. In the future, tools will better "understand" information and highlight complex patterns and relationships based on the user's area of interest.
Another way to reveal patterns and relationships among seemingly unrelated sets of information is with visualization tools, which convert numerical and textual information into graphical representations. Current visualization tools are somewhat limited, providing relatively simplistic projections of information onto 2- or 3-dimensional planes. In the future, tools will depict information in ways that are more intuitive for users to interpret and navigate. Virtual reality technology already exists, and although limited, provides the promise of enabling us to see information in a new, active, multisensory manner.
Other tools can help analysts and customers rapidly assimilate a large amount of information. Although abstraction and summarization tools are fairly crude today, in the near term they will allow us to determine whether specific kinds of information (e.g., people, specific activities, political organizations) are present in the information space. The enabling technologies for fusing and synthesizing information from different subject domains, in different languages, and various formats are emerging and providing a basis for users to generate high-fidelity simulations and models using information distributed across large network environments. In the future, these tools will have the capability of "understanding" a greater variety of concepts and "new media" (e.g., images, audio).
Collaborating
The intelligence enterprise of the 21st Century will be one that prizes collaboration for the synergies and efficiencies it can provide across increasingly parallel phases of the intelligence cycle. Indeed, the need for increased collaboration among the members of the enterprise and its customers is an idea that is already recognized. Congressional staff of the Permanent Select Committee on Intelligence of the 104th Congress called for a virtual analytic environment. The military intelligence services also speak of a future for the intelligence community that demands sharing of information and knowledge. The concepts of information dominance from Joint Vision 2010 are an indication that the Department of Defense understands the value and power of distributed collaboration.However, our ability to collaborate over a distance today is somewhat limited. In some cases cultural factors are obstacles; however, in others ad hoc communications include telephone, some electronic mail within agencies, and online "chat" software facilitate collaboration. We have some electronic meeting tools and other groupware capabilities, but in many cases these are proprietary solutions that are not practical for use across a large distributed enterprise. "Telepresence" is generally limited to studio-based video teleconferences, although desktop video teleconference capabilities are becoming increasingly available.
To achieve the vision of a more agile intelligence enterprise, more effective secure wireless personal communication devices, groupware and group decision tools are needed that support large numbers of people working in heterogeneous software and hardware environments. Robust telepresence capabilities that better provide the dynamics of face-to-face interaction and adaptive intelligence agents that can work on our behalf and collaborate with other such agents are also needed. Most important, organizational leaders must establish new incentives for their components to collaborate and cooperate with other organizations in the increasingly competitive fiscal setting of the coming decade.
Locating People, Organizations, and Services
The vision for a more agile intelligence enterprise relies heavily on all components of the Community working together and with our customers to exchange information, consult with each other, and work toward common goals and missions. However, if relationships cannot be established among people and information because they cannot be located or because they refuse to participate collaboratively, then the quality and quantity of our collaboration (and our missions) will suffer.
We must have the capability to contact and communicate with the customers that need our help and with our colleagues who can help us help them. Today our ability to find people and services is usually limited to static online and paper directories that may or may not be complete and accurate. Also, we often need to know more about an individual or service than the organization and phone number typically provided by current directories. Such information as security authorizations, areas of expertise, organizational role and position, personnel records, service and equipment manuals and instructions, and other properties which are uniquely bound to the people and services could be crucial in staffing and equipping a crisis team.
In the future we will need smart and robust directory services. These sophisticated electronic "white pages" and "yellow pages" will enable us to locate people sources and services based on deeper semantic understanding of not only the current position of the individual and the mission he or she is performing, but of that individual's background, training, and areas of expertise. We believe that much of what we must do today to find appropriate people and services will be handled by more robust search engines, and processing algorithms. For example, in the future, an enterprise member may need a subject matter specialist immediately to become part of a crisis management team. In addition to providing information about people whose skills match this requirement, we will want our directory services capability to be able to locate that person immediately, regardless of his or her location (at home, at work, on travel, or somewhere in the information space), and have him or her contact the cognizant authority.
Protecting Information Integrity and Privacy
For the enterprise to realize its full potential and extract full value from its resources, increased collaboration, interoperation and access across the various domains and compartments of the Intelligence Community must be promoted and enabled. However, as more information becomes available to more users over increasingly complex networks, the risks to that information and related information services both from insiders and outsiders will also grow.
In this environment, the protection of information and information service will be a function of both information security and information quality. To secure our information, we will have to make provisions for the confidentiality, integrity, and availability of that information in a highly dynamic and distributed environment. Secure information, however, is not necessarily trustworthy information. So in order for the enterprise to use its information with confidence, we will also need to make provisions for quality.
The information security needs of the intelligence enterprise will have much in common with those of other global enterprise emerging on the Internet. Many will share a need for very flexible and highly robust automated and distributed security services transparent to the user. Satisfying these security needs will require flexible security frameworks, higher-speed cryptographic equipment, dynamic access control mechanisms, network-based authentication, public key and digital signature technology, firewall and guard technology, security-enabled applications, sophisticated intrusion detection capabilities, intelligent security agents, integrated information protect capabilities, and robust, network-based security management tools. Where they provide these services, the security capabilities being promoted by the Internet community and commercial industry will offer opportunities for emulation and adaptation by the Intelligence Community.
Information integrity will also be an important consideration as a broader set of information spaces, both internal and external to the enterprise, become accessible. We must be able to trust our information if we are to collaborate responsibly and use it safely. In this environment, the challenge is more than simple data integrity. It includes having verifiable information about the source, being able to trace the pedigree of the information, understanding the context in which the information is valid, being aware of the volatility of the information, and protecting ourselves from both the deliberate and the inadvertent introduction of misinformation. Since human judgment will always be an important factor in assessing the integrity and value of information, we will also need the capability to make and verify assertions about the information (e.g., endorsements from a domain authority or a subject area expert). We will therefore need policies and mechanisms for reliably and rapidly indicating, disseminating, and determining the integrity of the information on which our enterprise will depend.
Security, therefore, is a critical enabler of the information sharing vision for the Intelligence Community. Though it must be recognized that some information about sources and methods will always be sensitive, due to operational vulnerabilities, requiring tightly controlled access restrictions to a select set of users to many intelligence products; striking a balance between information protection and information sharing, will be a significant but necessary challenge. Even with greater breakthroughs in technology, these challenges in dynamically maintaining this balance cannot be overcome without comprehensive and coherent information security policies and directives by appropriate authorities.
A Common Telecommunications Infrastructure
An agile enterprise needs a robust telecommunications infrastructure with assured availability, guaranteed quality of service, architectural scalability and, affordability, and the capacity to support for a whole host of emerging information service requirements.
Most users today cannot be certain that bandwidth will be provided where and when it is needed, or, in some circumstances, in a form that is technically compatible with their equipment. The problem is particularly acute outside of the continental United States, particularly in the Third World and war-torn environments, where commercial coverage and performance are often inadequate. As a result, connectivity from national sources and services to deployed (remote) operations must be improved.
Currently available telecommunications services are somewhat scaleable and flexible, but end-to-end interoperability problems exist, networks are difficult to expand or reconfigure, and there is limited means to reallocate bandwidth among users and functions (e.g., among video, data, and voice services). The current ability of the telecommunications infrastructure to support the growing information system services such as collaboration and teleconferencing, distributed database access and retrieval, electronic mail, facsimile, graphics and map transfer, imagery dissemination, office automation, remote terminal support, video broadcast, voice, wireless, and web services, varies widely today.
Clearly, the agile enterprise will need a variety of robust, bandwidth-on-demand communications services, from terrestrial to satellite, including wireless solutions, to be able to meet the demands that will be placed on it by an information sharing and collaborating user base.
An Integrated Information Space
In planning for a more agile enterprise of the 21
st Century, with dynamic information sharing services and capabilities, parts of the information space will need effective tight control and parts will not. Controls are brought to bear mostly to optimize the nature and use of the local information space within an agency or command. For example, establishing standards and practices will assist the user in carrying out his or her job in as automated and seamless manner as possible while interacting with others at distant locations.However, a more open, shared and adaptive information environment supports the enterprise by providing access to information spaces and sources far removed from traditional Community information stores. An enterprise member may consult an ever widening circle of information domains starting with the tightly controlled, well regulated information stores of the enterprise, and growing out into the Internet at large, and foreign, private, government, and commercial information spaces.
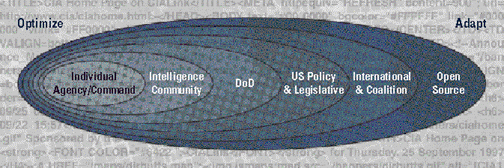
As we move outward into a broader Government-wide information space and into other jurisdictions (e.g., coalition forces) including the entirety of the Internet, we have increasingly less control over the information or the information services. While this means that we might not realize the benefits of well regulated information and metadata in some parts of the information space, the enterprise will have access to a much greater and richer set of information resources.
We must, therefore, establish the capability to optimize our local spaces while ensuring that we take advantage of the wide variety of information available in the world wide information market. To do this, we must ensure that our business processes and our procedures remain agile enough to permit us the flexibility to do both. We also must not inadvertently impose standards or procedures that either take us out of the mainstream or prevent us from interoperating with the larger world. Authorities and interagency bodies must have the flexibility to revise and update standards and procedures, as needed, to keep pace with the wider environment.
"The status quo approach to information management-invest in new technologies, period-just doesn't work. Instead, managers need a holistic perspective, one that can weather sudden business shifts and adapt to ever-changeable social realities. This new approach, which I call information ecology, emphasizes an organization's entire information environment."
Thomas H. Davenport,
Director (with Laurence Prusak)
Information Management Program,
University of Texas
Information Ecology: Mastering the Information and Knowledge Environment, 1997
Facing the Challenge-Seizing the Opportunity...
Sound intelligence collection, analysis, and reporting have long-contributed to the nation's security and economic well-being. Accurate, detailed, and comprehensive intelligence was a significant factor in ending the Cold War and in winning the Gulf War. Continued intelligence production will be vital to averting the next war, or at least to minimizing the number of casualties in future conflicts. Also, extensive and precise foreign intelligence will be crucial to future diplomatic negotiations, economic planning, and treaty verification. Targeted intelligence will also be critical to law enforcement, fighting international organized crime, countering the terrorist threat, and waging a successful war on drugs. Moreover, intelligence will continue to prove useful in responding to natural disasters and protecting our environment.
Though the U.S. Intelligence Community is the best in the world, there is much work left to do to adapt to the new world order, a new millennium, and the shifting demands resulting from our new and evolving National strategies and priorities. We must respond to these challenges to our security and supremacy during a period of declining resources.
However, we share a collective vision for information and knowledge management with much of the industrial and commercial world from whom we can learn and benefit. In general, we envision a shared electronic, virtual information space, supported by a dynamic and robust "information marketplace," in which intelligence collectors, analysts, military and law enforcement operators, and policymakers all collaborate, interact, and share resources.
In seizing the opportunity, we must work closely together to pursue three broad objectives:
•
To begin, in earnest, to manage our information as a critical Community resource for the benefit of our customers and the efficiency of our operations•
To cost-effectively exploit the opportunities offered by information technology, equipping and empowering our professional intelligence knowledge workers with modern tools to enhance productivity and increase the utility of our products and services•
To establish and apply strategies for more prudent investments in information technology across the Community that enable us to better share information as an enterprise and better serve our customers and support our missionAll three objectives must be pursued always in context with increasing the mission effectiveness of our customer base-the policymakers, our military commanders, the law enforcement agencies, and the counter intelligence community. Achieving these objectives will open up opportunities for new and improved ways of doing business, providing many more avenues for sharing, valuing, and managing intelligence information within our individual agencies and across the enterprise.
Manage Our Information as a Critical Community Resource...
To meet the challenge of shifting mission priorities while achieving our national security objectives, we must provide our mission customers with the intelligence information and knowledge they need, when and where needed, and in the context required to support the decisions to be made. To accomplish this, there is no question that we need to work more collaboratively than we have in the past as a unified, virtual intelligence enterprise. In doing so, to make our information accessible to those who need it and are authorized to view it, we must maintain the agility to tailor, combine, and adapt data and information from multiple sources and various forms into the context and presentation format that meet the immediate needs of the decisionmaker.
Our first objective should be for the Community (internally) to manage its information as its most critical resource for the benefit of its customers and the efficiency of its operations as an enterprise. This requires us to think a bit differently about the information we require, and the knowledge we enable, and how we a value it. In the past, we largely focused on information systems, which were considered major capital assets due to their expense and long lead-time to develop and acquire. This has changed not only with the accelerating pace of technological development and the rate at which today's systems become obsolete, but with the rapid decline in prices for systems. Today's systems are becoming commodities or consumables that require replacement or upgrade much more frequently than was the case in the past.
Information, itself, is the true capital resource of the enterprise, both from an economic and functional standpoint. The right information at the right time and in the right form and context permits us to make sound decisions and conduct our business more effectively and efficiently. Information needs to be invested in and managed as we manage other resources and to other resource requirements. As we prepare to enter the 21
st Century, we must explore how best to shift our focus from a systems-centric perspective to a knowledge-based information-centric perspective.The value of this resource varies depending on its nature, use, and context. It is difficult to put a dollar value on information. In certain situations, information may be priceless (averting hostilities, saving lives, etc.). Some information depreciates quickly, while some has long-standing archival value. Some even appreciates over time and may have more or different value based on changed future circumstances. And, as other assets, information has a cost associated with acquisition, manipulating it, publishing it, storing it, accessing it, applying it, and providing it to others who need it. Like most capital resources, it must be secured against theft, tampering, misuse, corruption, and destruction.
In order to better manage information as a resource, we need to determine how best to apply information resource management concepts to the business of intelligence. This will involve gaining a better understanding of these concepts and weighing their advantages against their possible effect on our missions. We also need a better feeling for how an information marketplace might work in our environment, and what types of controls we would need to impose to ensure that we still have all the information we need as a Community to support each other and our customers. Cross-Community information management task forces (including mission-customer membership), senior level advocacy and steering groups, and pilot projects to test the concepts and assess the customer needs and commensurate enterprise capabilities offer opportunities that should be exploited.
We need not start "from scratch." We have an excellent start toward an agile and collaborative enterprise with the Intelink service, in operation since late 1994, and the tremendous progress being made to increase information agility and collaboration within individual organizations. We must exploit these collective accomplishments as a point of departure and test bed in which to examine whether and how we might devise a practical measure of information value which could be used to evaluate progress and to drive future acquisition and budget allocation decisions. Further-more, we must establish a common information inventory process that can be used within our respective environments, as well as across the enterprise. This inventory (architecture or information model) can help us identify and characterize our information resources. An information model can help us evolve toward a more agile enterprise and ensure that future, unknown information needs are met (e.g., global coverage of potential trouble spots).
In addition, policies, processes, and procedures need to be revisited and revised. For example, each of us will need to ensure that our organizational leadership interests, motivation processes and personnel incentives will encourage a culture of information sharing and collaboration. Policies will also need to determine when the results of a collaboration between analysts and customers become an official intelligence product. As organizational hierarchies are rendered less important by network-based information technology, we in the enterprise must address how and when authority and responsibility get redistributed. Similarly, security ground rules for what knowledge should or should not be shared must be reexamined.
Each organization must explore the new paradigm of providing ourselves and our customers with dynamic access to, reuse of, and repackaging of selected information holdings (e.g., fragments, data bases, or libraries) to provide the context tailored to the need at hand, instead of providing only "finished" intelligence products. While there will always be a place for finished intelligence products, we must recognize the burgeoning demand for rapid, yet prudent, access to pertinent knowledge fragments in support of fast-breaking situations. However, mere electronic access to vast data bases by customers is not a complete solution; we must determine where value-added analysis is necessary to achieve correct interpretation of the information by customers and provide linkages to appropriate analytic resources (e.g., analyst or expert names, manipulation and visualization software, or predictive models) to assist in that interpretation.
Collaboration is another area with substantial implications for our infrastructure, security, and management processes. While we install the infrastructure to provide the necessary connectivity services, we need to do more to address the integration of collaborative interaction with our "digital" resources. The collaborative model includes electronic knowledge sharing (such as via a network) as well as human-to-human communications (such as via telephones or video conferencing). Just as today, where there are sign-off requirements for release of an intelligence product, in the future, documented evidence of collaboration may be required prior to acceptance by customers of analytic conclusions; or at least such evidence may contribute to increasing their confidence in the validity of the intelligence product provided.
All institutions must advance to keep pace with the times or face extinction; the Intelligence Community is no exception. The principal objective must be to provide the right information to the right people at the right time. To succeed in the 21st Century, we must work together, collaboratively as an integrated enterprise, to optimize the value of the information we are providing, the agility in forming it into the context needed, and the accessibility of our products and services to those needing them.
Exploit the Opportunities Offered by Information Technology...
Our second objective ought to be to ensure that we cost-effectively exploit
the opportunities offered by information technology. Information technology will
be both a driver and a solution to our information and knowledge production
needs. With technology advances, customers will expect more in terms of
information products, access, and manipulation. Analysts will demand more from
their information systems in terms of convenience of operation and exploitation
of a wider variety of information sources (as well as support for distributed
collaboration with customers and other analysts). And finally, all of us will
need better tools to assess the validity
of information as we increase our
use of open services and sources.
Convenient and affordable access to information technology outside the workplace will continue to raise our expectations and demand for similar capabilities in the office. The more technology that is available, the more we will use it; the more we use it, the more information and agility we can make available; and the more information and agility we make available, the more challenging will be the problem of managing the increasing volume of information to produce the knowledge needed by our customers.
As large amounts of communications bandwidth become increasingly affordable, the network will no longer be the bottleneck. It will one day be practical to get massive amounts of information all the way to the edges of the network (e.g., to the foxhole, or the cockpit, or the observation post). However, in the nearer term, the amount of information to be passed over this network will grow just as exponentially as the growth in bandwidth and processing technology. But, both now and then, we must take care to not flood our customers with information. We must manage information and deliver only knowledge needed by those customers.
Security, of course, will continue to be an extremely vital part of the information technology equation. The growing threat of hostile information operations against the Community as well as the entire national infrastructure is also causing us to enlarge our mission. Each step towards greater automation of our intelligence information resources must be taken in light of the risk of information warfare. Many new security capabilities are emerging from technology advances in the private sector, which are urgently needed and must be exploited to support our own security management infrastructure.
Change will continue to run rampant, not only in technology but in missions and targets, too, and the successful intelligence enterprise will be one which learns to be agile and keep up. We have witnessed the proliferation of Internet technology around the globe. This trend will continue, with more and more advanced information and networking technologies adopted by foreign nations, well-funded international crime syndicates and terrorists. In addition, in today's world, nations are leapfrogging whole generations of technology as they upgrade their internal infrastructures. Indeed, some countries are finding it easier and more cost-effective to skip laying twisted pair telephone wires and jump immediately to large scale implementation of cellular telephones. Some of these nations may be tomorrow's adversaries.
We cannot shy away from information technology and the constant upheaval caused by technological innovation; it is futile to try to "future-proof" our operations. Also, personnel costs (labor) are crowding out other cost categories of the intelligence enterprise. Commercial business is driving information technology, and we must continue to modernize our policies and procedures (such as evolutionary acquisition practices) to keep pace. We must continue to pursue the philosophy of applying commercial information technology wherever feasible.
Improvements in productivity, as offered by modern information technology, are essential. As components of a more
agile intelligence enterprise, we must adopt sharing of roles with respect to monitoring specific areas of information management technology and in presenting recommendations to the enterprise regarding implementation. Our best "technology insurance" comes from staying flexible and informed and by embracing a practice of strategic planning and continual modernization of our information systems and the functional processes they support as an integrated enterprise.
Invest More Prudently in Information Technology...
Our third objective should be to establish and execute a plan for prudently investing in information technology across the enterprise to enable us to share information and better serve our customers. We must, individually and collectively, ensure prudent investments in information technology and people, both now and into the future. Information technology will be vital to the business of intelligence, as it will be for our customers in using the intelligence we provide.
Planning a comprehensive information technology strategy is the key to the cost-effective conduct of the intelligence business. Most Intelligence Community organizations already have an information technology strategic plan that identifies systems and services that will be provided, in concert with the management principles of the Clinger-Cohen Act. In addition, an Intelligence Community enterprise-wide information systems strategic plan is now being published.
Our information systems strategic planning must be driven by an understanding of the information technology marketplace (what capabilities will be available and which approaches and product-lines will survive). It must also be derived from an understanding of the information we have, its location, its form, its currency, and its intended use. Further, it must be consistent with a comprehensive information security model, yet to be developed, that defines rules, strategies, and degrees of freedom for entertaining candidate technologies and capabilities for our information and information management services.
Finally, our strategic planning process must be sensitive to some realities
that could actually impede our progress as an integrated and interoperable
enterprise as we move forward as individual components of the enterprise. For
example, well-intentioned but non-coordinated decisions regarding the selection
and implementation of available technology and services could adversely impact
our ability to interoperate. Security standards are critical, particularly to
dissuade agencies from resisting interoperability opportunities in the name of
protecting sources and methods. Components who can afford to progress faster
than others could create significant gaps in capability and interoperability.
Thus, an essential element of our strategic plan should be a carefully
constructed, well-coordinated, and often-revisited evolutionary transition
strategy that defines incremental capability milestones and agreements. This
will allow us to consider specific capabilities, implementation criteria, and
opportunities for sharing across the Community, while maintaining backward
compatibility with components operating at lower levels. Such an evolutionary
strategy is outlined by Figure 4.
Conclusion
The Intelligence Community faces turbulent times and many challenges ahead, yet times that afford more opportunities to excel than ever before. To thrive-or survive-and provide increasing value to our customers, we must interact more closely, share our information and knowledge, and help each other and our customers reach the best decisions possible, all while avoiding costly and unnecessary restarts, redundancies, and system incompatibilities. We must forge stronger ties with commercial industry and leverage their products and strengths. We must pay closer attention to the knowledge needed by our customers and structure our processes and systems to provide the products and the services to fulfill those needs in the most cost-effective manner. We must do an even better job of collecting the right data for analysis, and providing the right information in the right format and context to the right customers in time to be of real use.
Afterword
To achieve the agile collaborative enterprise that is our vision, we must become more agile as individuals, as agencies, and as a Community. We must establish and evolve a capacious and interoperable information infrastructure, within and among the intelligence agencies, one that supports collaboration and knowledge sharing among our members and our customers. We must learn to manage risk effectively, not avoid it. We must acquire, install, and operate systems that are driven by changing intelligence mission needs, and we must account for our resource expenditures in ways that can identify the value received for the resources expended. We must instill organizational and individual motivations and rewards that are consistent with our goals for greater sharing and working together. We must recognize the need to keep the knowledge-based skills of our workforce up-to-date and to provide each intelligence knowledge worker with timely feedback and an adequate understanding of the value of his or her contributions to the enormous and diverse intelligence enterprise. We need systems that are able to adjust to rapidly changing world conditions. We need innovative and adaptive staff able to identify and provide relevant and tailored intelligence knowledge products and services needed by our customers. Finally, we need organizations that are able to evolve in response to a highly dynamic, constantly changing provider-consumer intelligence knowledge marketplace.